The ability to digitally prove who you are on a national scale across the private and public sectors has the potential to improve user experience, strengthen security, and boost economic growth. For the consumer, it’s about simplicity, transparency, personal control of data, and reliability.
The European Commission proposed a framework for a European digital identity in June 2021, which would be accessible to all EU citizens, residents, and businesses via a European digital identity wallet.
The opportunities for governments and businesses are numerous. Banks and governments have a large stake in the digital identity narrative, whether it's offering digital identity services that consumers can use across organizations and borders, or simply allowing the user to access more services more seamlessly with convenient online identity verification and authentication.
In this article, we break down the fundamentals of what an electronic digital identity (eID) is, as well as the stringent controls that form a part of the digital identity process.
1. The three necessary steps toward obtaining a Digital Identity
Who are you?
Step 1. Capturing attributes such as ID documents or biometric data
This entails collecting, validating, and verifying identification evidence and information about a person; establishing an identity account, and binding the individual's unique identity to authenticators owned and controlled by that person.
You are you
Step 2. Verifying the authenticity of documents
This establishes, based on the possession and control of authenticators, that the individual is truly who he or she claims to be.
Here I am!
Step 3. Digitizing Identity
The personal information from the ID is then linked to attributes via an identity-proofing digitization process. This data cluster is then saved as a digital ID.
2. The purpose of identity proofing
Identity proofing's ultimate purpose is to confirm that a user's claimed identity matches their actual identity: that their identity is authentic and not false. Identity proofing is important for all cases where trust in the identity of a natural or legal person is essential.
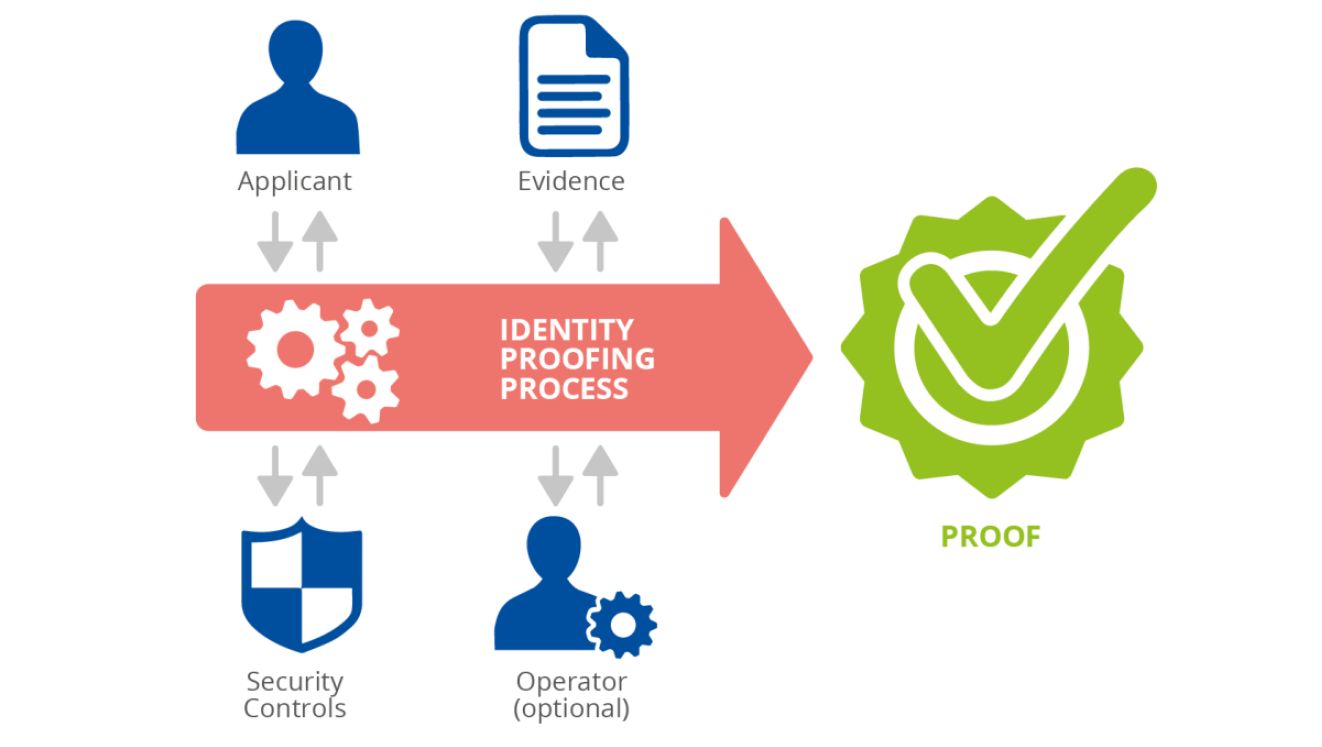
Infographic: Identity Proofing Entities (source: ENISA)
The Electronic Identification, Authentication, and Trust Services (eIDAS) Regulation (EU) No. 910/2014, known as eIDAS (electronic IDentification, Authentication, and Trust Services), introduces provisions for electronic identification as a major lever for the digital market across Member States.
Electronic identification, as defined by eIDAS, is a digital solution that enables individuals or organizations to access online services or perform electronic transactions by providing proof of identity. It specifically allows alternatives to physical presence for identity proofing in the context of granting qualified certificates and opens the door for remote identity proofing under article 24(1) (section 1.3).
|
Methods for remote identity verification make it possible to identify people without their being present physically in the same space. The user experience can be enhanced and cross-border services can be developed. This opens a new level of economic potential if there is trust that the identity proofing was done in a trustworthy and secure way. |
Remote identity proofing can be used by qualified trust services (as defined in the eIDAS regulation) to issue qualified certificates, identify the sender or receiver in qualified electronic delivery services, or by a qualified trust service managing the key for the user to ensure that access to the key is provided to the same person as identified in the corresponding certificate.
3. Certificate-based Identity
Certificate-based identity is a method based on an internal or third-party trust service and the evidence provided by this service, such as electronic signature certificates and seals. The certificate is used to retrieve the person's identification data. The identity verification system's interaction with the trust service provider is confined to certificate revocation checks. This is frequently accomplished through the use of a qualified electronic signature or seal, or an enhanced electronic signature based on a qualified certificate.
The certificate-based identity proofing process
When using remote identity proofing to issue qualified certificates, the initial identification binding and verification is performed by a human operator who follows documented instructions:
|
Initiation |
Attribute and evidence collection |
Attribute and evidence validation |
Binding and verification |
Issuing of proof |
|
Information about the process Presentation of the policy, and terms and conditions Signature creation application download and initialization |
Random, one-time data presentation, and its signing Data signing Signing certificate collection Additional retrieve of data from internal and external data sources |
Certificate validity and revocation verification Validation against internal and external databases |
Trust anchors checks Data completeness confirmation Identification data and attributes binding |
Automatic proof |
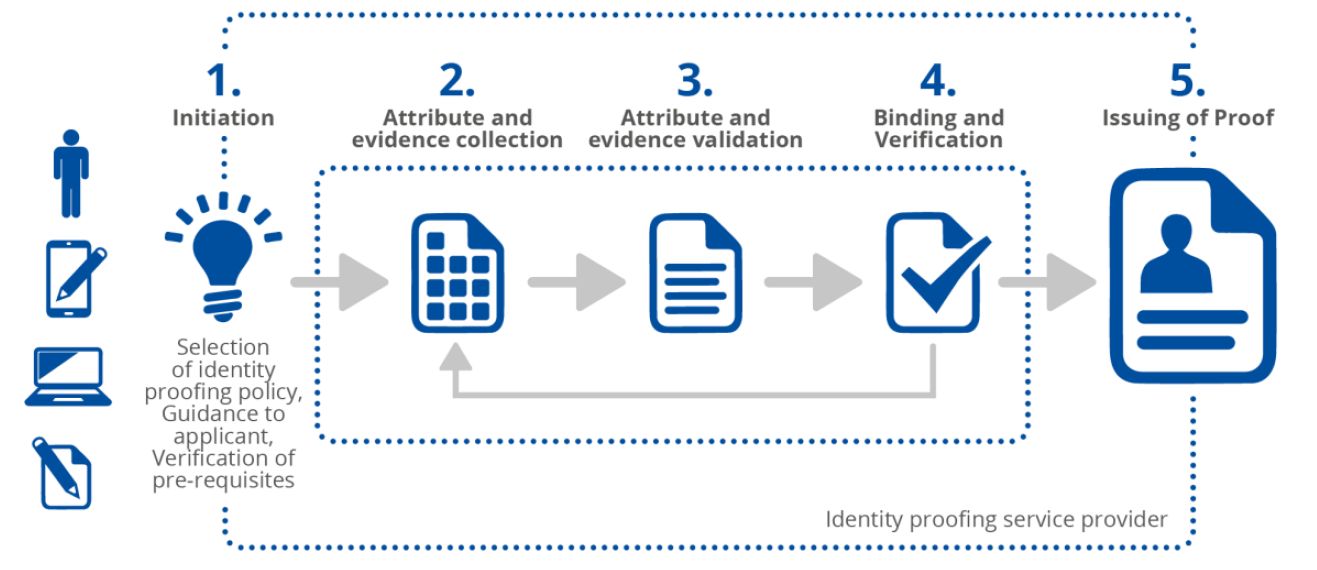
Infographic: General Identity Proofing Process (source: ENISA)
4. Digital identity wallet process
People and organizations can utilize their digital identities to access services online. These pieces of personal or organizational data are also referred to as attributes.
As part of a 'digital identity system,' digital identity services rely on relationships between individuals or users and service providers.
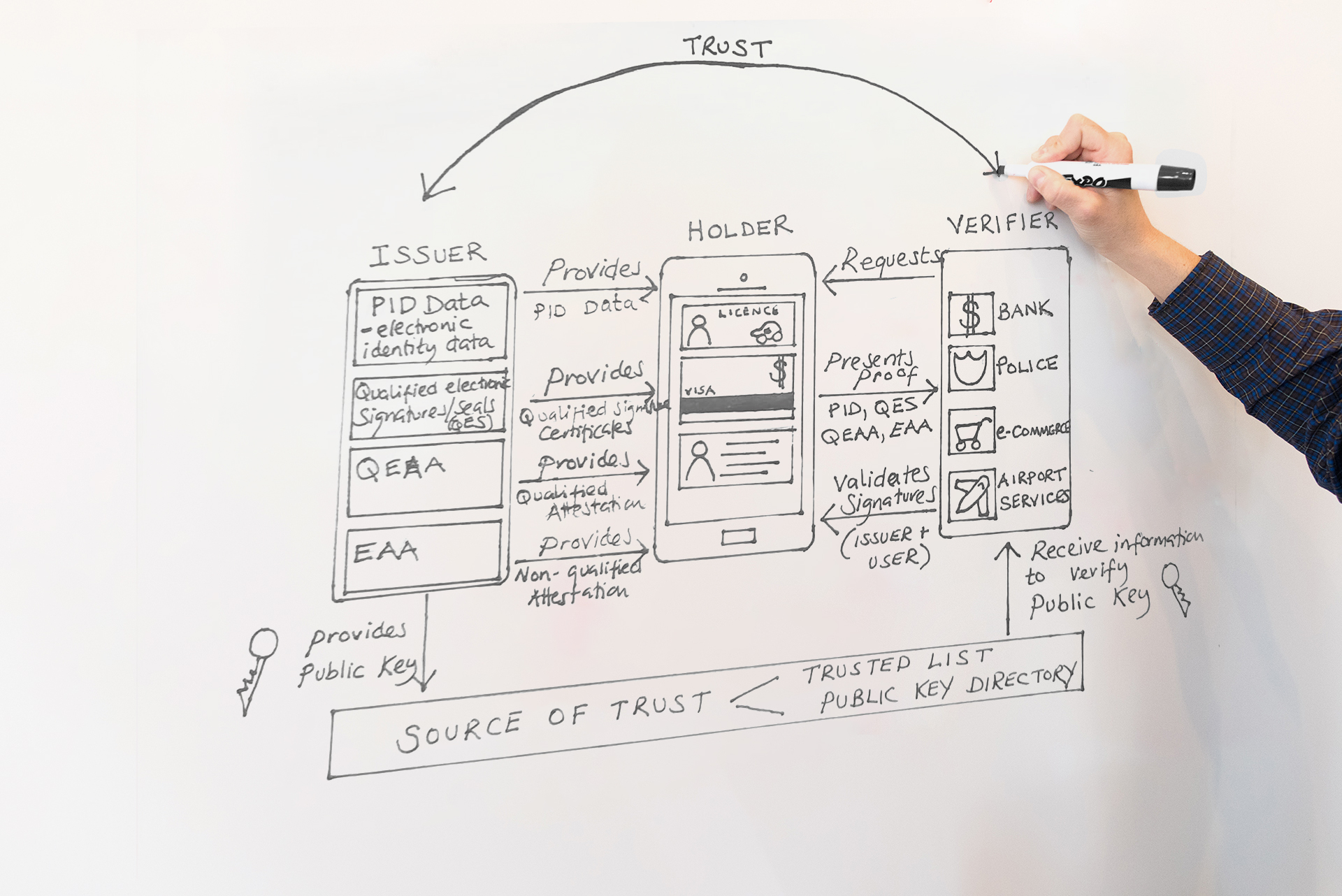
The digital identity system consists of all of the participants, their roles, and activities to allow users to communicate information in a safe and secure manner. The following illustration details how the signature certificates are mapped into the identity architecture:
Inspired by: lissi
The illustration details how the Wallet should have 4 functions:
-
Identification and authentication,
-
Verifiability of the validity of the evidence by third parties throughout Europe,
-
Secure storage and presentation of verified identities and their data and
-
Generation of qualified electronic signatures.
Until now, the eIDAS regulation has only focused on online identification. However, the new proposal – eIDAS 2.0 – aims to extend identity to the world of physical services which can be accessed from anywhere around the globe. As a result, a secure, trusted, and efficient identification process is required to give customers a seamless experience while enrolling in, utilizing services, or purchasing products.
The updated eIDAS 2.0 initiative is carried out by the European Commission. This new eID strategy is built on the existing cross-border legal framework for trusted digital identities, the European electronic identification and trust services initiative (eIDAS Regulation), which was adopted in 2014. The eIDAS Regulation establishes the framework for cross-border electronic identification, authentication and website certification within the European Union.
Digital identity eID has the potential to make it easier for financial institutions to meet legal duties in the areas of Know Your Customer (KYC), anti-money laundering (as defined by the 4th Anti-Money Laundering Directive, 4AMLD), and robust authentication of parties (as per the Payment Services Directive 2, PSD2).
By September 2023, all EU member states must ensure that a Digital Identity Wallet (DIW) is available to all EU citizens, residents and businesses in the EU and usable not only for identity documents but for all attestations, including those with sensitive personal data, such as health-related data and documents.
SkyRadar & Cybersecurity
SkyRadar stays ahead of all current topics across cybersecurity structures and challenges, identity and threat intelligence that affect all industries from aviation to telecommunications, through to IoT.
You can train your aviation team by working with SkyRadar, which provides an ATSEP Cybersecurity Training Module. It meets international training standards set by ICAO and EASA.